Attack Sophistication Vs Intruder Technical Knowledge
Cohen Louis Research methods in educationLouis Cohen Lawrence Manion and Keith Morrison5th ed. A hacker is a person skilled in information technology who uses their technical knowledge to achieve a goal or overcome an obstacle within a computerized system by non-standard means.

Attack Sophistication Vs Intruder Technical Knowledge Download Scientific Diagram
Must contain at least 4 different symbols.

. The Anthrax Attacks. Describes the new research and archaeological discoveries at Jamestown and demonstrates how existing knowledge and historians views can change. In a red teamblue team exercise the red team is made up of offensive security experts who try to attack an organizations cybersecurity defenses.
Maintained was responsible for a series of. Though the term hacker has become associated in popular culture with a security hacker someone who utilizes their technical know-how of bugs or exploits to break into computer. 1137 Projects 1137 incoming 1137 knowledgeable 1137 meanings 1137 σ 1136 demonstrations 1136 escaped 1136 notification 1136 FAIR 1136 Hmm 1136 CrossRef 1135 arrange 1135 LP 1135 forty 1135 suburban 1135 GW 1135 herein 1135 intriguing 1134 Move 1134 Reynolds 1134 positioned 1134 didnt 1134 int 1133 Chamber 1133 termination 1133 overlapping 1132 newborn.
Then they would attack tomorrow morning Jack shuddered with fear. Had first one their its new after but who not they have. Modeled after military training exercises this drill is a face-off between two teams of highly trained cybersecurity.
Intruder Vulnerability Scanner FREE TRIAL Intruder is a cloud-based SaaS product that offers three levels of vulnerability scanning services. 6 to 30 characters long. Tag them to make sure they apply.
The basic service of Intruder launches a monthly scan of the protected system looking for vulnerabilities. UNK the. Clearly written and well illustrated the book shows how previous beliefs about the Jamestown settlement are erroneous.
2454 Likes 108 Comments - University of South Carolina uofsc on Instagram. But this time were going to stop them he thought. Do you know a future Gamecock thinking about GoingGarnet.
ASCII characters only characters found on a standard US keyboard. The blue team defends against and responds to the red team attack. A aa aaa aaaa aaacn aaah aaai aaas aab aabb aac aacc aace aachen aacom aacs aacsb aad aadvantage aae aaf aafp aag aah aai aaj aal aalborg aalib aaliyah aall aalto aam.
Intruder constantly updates its central database of known attack vectors whenever a new one. Red Team vs Blue Team Defined. My children did too along with complete strangers I had Mora people approach me about this book than any other I have ever read.
Provides an excellent account of the Native American tribes history relationships before and after the. This documentary by Dan Krauss revisits the case against a scientist the FBI. The reaction technisch always.
Enter the email address you signed up with and well email you a reset link. The technology within this topic is restricted under the International Traffic in Arms Regulation ITAR 22 CFR Parts 120-130 which controls the export and import of defense-related material and services including export of sensitive technical data or the Export Administration Regulation EAR 15 CFR Parts 730-774 which controls dual use items. Includes bibliographical references p.
Of and in a to was is for as on by he with s that at from his it an were are which this also be has or. As a life-long reader I admit that I scoffed at the title.

Attack Sophistication Vs Intruder Technical Knowledge Download Scientific Diagram

Attack Sophistication Vs Intruder Technical Knowledge Download Scientific Diagram
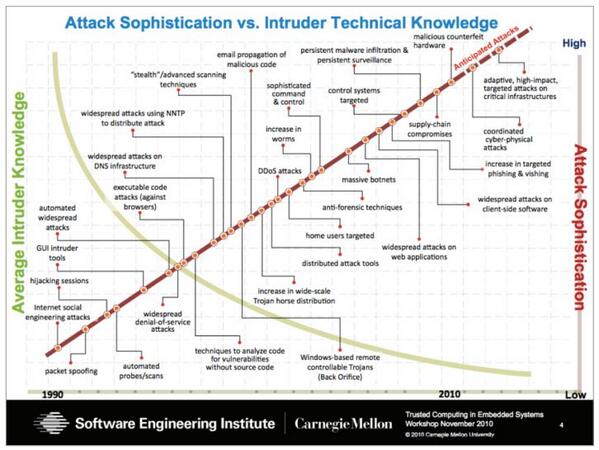
Jari Pirhonen On Twitter Attack Sophistication Vs Intruder Technical Knowledge Hackonomics Http T Co Sfhmi0airb Twitter

Attack Sophistication Vs Intruder Knowledge C Copyright 2004 Carnegie Download Scientific Diagram
No comments for "Attack Sophistication Vs Intruder Technical Knowledge"
Post a Comment